1 OKR examples for Computer Security
What are Computer Security OKRs?
The Objective and Key Results (OKR) framework is a simple goal-setting methodology that was introduced at Intel by Andy Grove in the 70s. It became popular after John Doerr introduced it to Google in the 90s, and it's now used by teams of all sizes to set and track ambitious goals at scale.
Writing good OKRs can be hard, especially if it's your first time doing it. You'll need to center the focus of your plans around outcomes instead of projects.
We have curated a selection of OKR examples specifically for Computer Security to assist you. Feel free to explore the templates below for inspiration in setting your own goals.
If you want to learn more about the framework, you can read more about the OKR meaning online.
Best practices for managing your Computer Security OKRs
Generally speaking, your objectives should be ambitious yet achievable, and your key results should be measurable and time-bound (using the SMART framework can be helpful). It is also recommended to list strategic initiatives under your key results, as it'll help you avoid the common mistake of listing projects in your KRs.
Here are a couple of best practices extracted from our OKR implementation guide 👇
Tip #1: Limit the number of key results
The #1 role of OKRs is to help you and your team focus on what really matters. Business-as-usual activities will still be happening, but you do not need to track your entire roadmap in the OKRs.
We recommend having 3-4 objectives, and 3-4 key results per objective. A platform like Tability can run audits on your data to help you identify the plans that have too many goals.
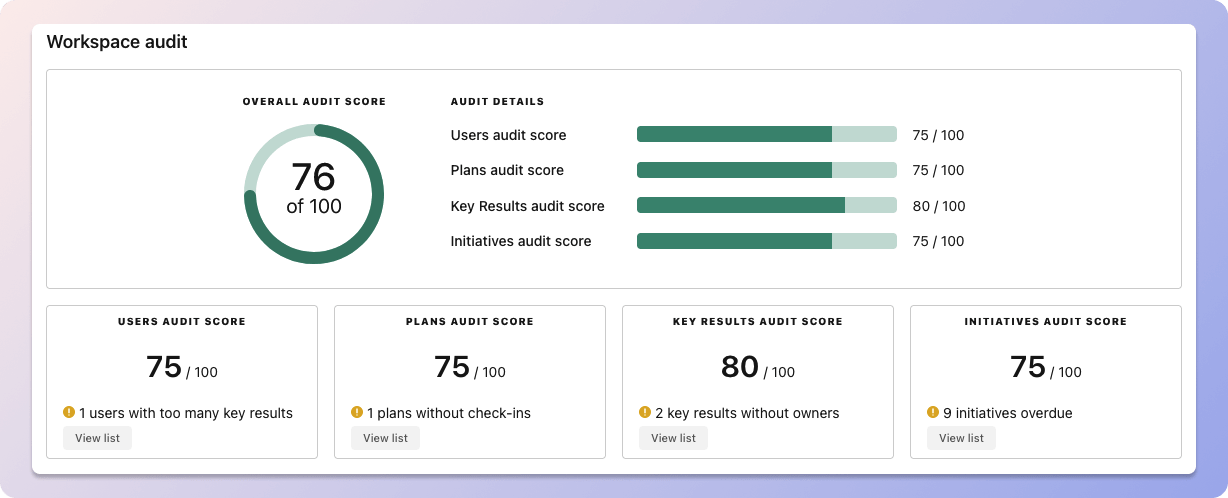 Tability's audit dashboard will highlight opportunities to improve OKRs
Tability's audit dashboard will highlight opportunities to improve OKRsTip #2: Commit to the weekly check-ins
Don't fall into the set-and-forget trap. It is important to adopt a weekly check-in process to get the full value of your OKRs and make your strategy agile – otherwise this is nothing more than a reporting exercise.
Being able to see trends for your key results will also keep yourself honest.
 Tability's check-ins will save you hours and increase transparency
Tability's check-ins will save you hours and increase transparencyTip #3: No more than 2 yellow statuses in a row
Yes, this is another tip for goal-tracking instead of goal-setting (but you'll get plenty of OKR examples below). But, once you have your goals defined, it will be your ability to keep the right sense of urgency that will make the difference.
As a rule of thumb, it's best to avoid having more than 2 yellow/at risk statuses in a row.
Make a call on the 3rd update. You should be either back on track, or off track. This sounds harsh but it's the best way to signal risks early enough to fix things.
Building your own Computer Security OKRs with AI
While we have some examples below, it's likely that you'll have specific scenarios that aren't covered here. There are 2 options available to you.
- Use our free OKRs generator
- Use Tability, a complete platform to set and track OKRs and initiatives
- including a GPT-4 powered goal generator
Best way to track your Computer Security OKRs
Quarterly OKRs should have weekly updates to get all the benefits from the framework. Reviewing progress periodically has several advantages:
- It brings the goals back to the top of the mind
- It will highlight poorly set OKRs
- It will surface execution risks
- It improves transparency and accountability
Most teams should start with a spreadsheet if they're using OKRs for the first time. Then, once you get comfortable you can graduate to a proper OKRs-tracking tool.
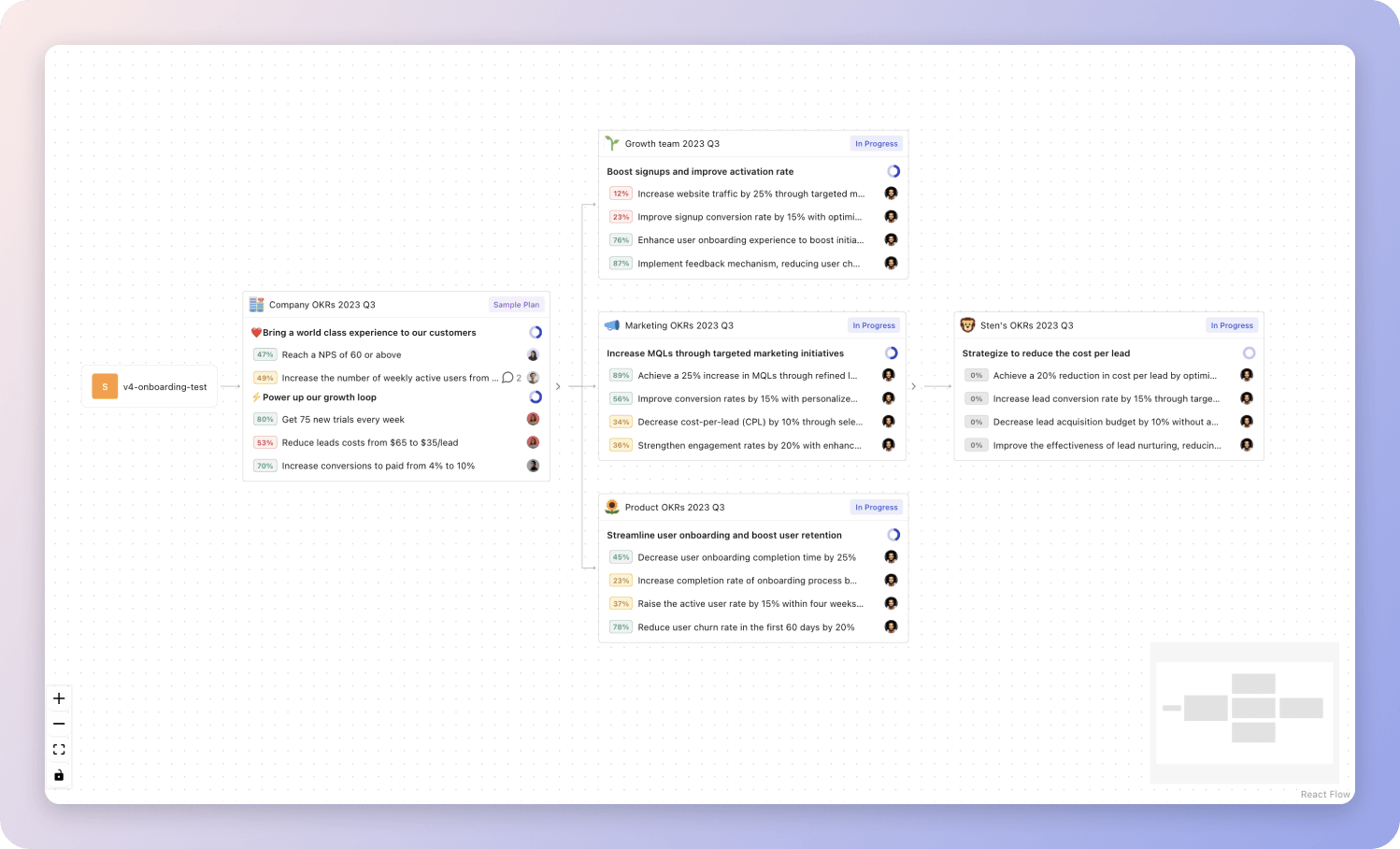 Tability's Strategy Map makes it easy to see all your org's OKRs
Tability's Strategy Map makes it easy to see all your org's OKRsIf you're not yet set on a tool, you can check out the 5 best OKR tracking templates guide to find the best way to monitor progress during the quarter.
Computer Security OKRs templates
We've covered most of the things that you need to know about setting good OKRs and tracking them effectively. It's now time to give you a series of templates that you can use for inspiration!
You will find in the next section many different Computer Security Objectives and Key Results. We've included strategic initiatives in our templates to give you a better idea of the different between the key results (how we measure progress), and the initiatives (what we do to achieve the results).
Hope you'll find this helpful!
OKRs to become a computer security expert
Become a computer security expert
Successfully pass the Certified Ethical Hacker (CEH) exam with a score of 80% or higher
Develop and execute a comprehensive security project, receiving positive feedback from industry experts
Collaborate with industry experts to gather insights and recommendations for improving security measures
Regularly monitor and evaluate the effectiveness of implemented security measures to ensure ongoing protection
Develop and implement robust security protocols and controls across all systems and processes
Conduct a thorough assessment of current security vulnerabilities and risks
Complete at least two online courses on computer security, scoring above 90% in each
Ensure mastery of course materials and aim to score above 90% in assessments
Devote dedicated hours per week to studying and completing the online courses
Research and identify two reputable online courses for computer security
Enroll in the selected online courses on computer security
Implement and manage effective security measures on personal computer resulting in zero malware incidents
Install a reliable antivirus software program on the personal computer
Enable automatic software updates for the operating system and all installed applications
Avoid clicking on suspicious links or downloading files from untrustworthy sources
Regularly update the antivirus software to ensure the latest protection against malware
More Computer Security OKR templates
We have more templates to help you draft your team goals and OKRs.
OKRs to increase sales through channel partners
OKRs to migrate to a new technology
OKRs to boost internal outreach and enhance brand recognition
OKRs to improve website security through effective deployment of content security policy
OKRs to improve code quality through effective code reviews
OKRs to drive Business Expansion in Saudi Arabia's school sector
OKRs resources
Here are a list of resources to help you adopt the Objectives and Key Results framework.
- To learn: Complete 2024 OKR cheat sheet
- Blog posts: ODT Blog
- Success metrics: KPIs examples